Docker
Prerequisites
You should have the following available on the system you are using to set this up:
Docker - https://docs.docker.com/get-docker/
git
curl
Hint
If at any point docker compose does not work, but docker-compose does, you have an older version of Docker (and Compose), please update before continuing. Be cautious of these two commands and any suggestions copy and pasted from the internet
Setup Guide
run
bash <(curl -s https://gitlab.com/allianceauth/allianceauth/-/raw/master/docker/scripts/download.sh). This will download all the files you need to install Alliance Auth and place them in a directory namedaa-docker. Feel free to rename/move this folder.run
./scripts/prepare-env.shto set up your environment(optional) Change
PROTOCOLtohttp://if not using SSL in.envrun
docker compose --env-file=.env up -d(NOTE: if this command hangs, follow the instructions here)run
docker compose exec allianceauth_gunicorn bashto open up a terminal inside an auth containerrun
auth migraterun
auth collectstaticrun
auth createsuperuservisit http://yourdomain:81 to set up nginx proxy manager (NOTE: if this doesn’t work, the machine likely has a firewall. You’ll want to open up ports 80,443, and 81. Instructions for ufw)
login with user
admin@example.comand passwordchangeme, then update your password as requestedclick on “Proxy Hosts”
click “Add Proxy Host”, with the following settings for auth. The example uses
auth.localhostfor the domain, but you’ll want to use whatever address you have auth configured on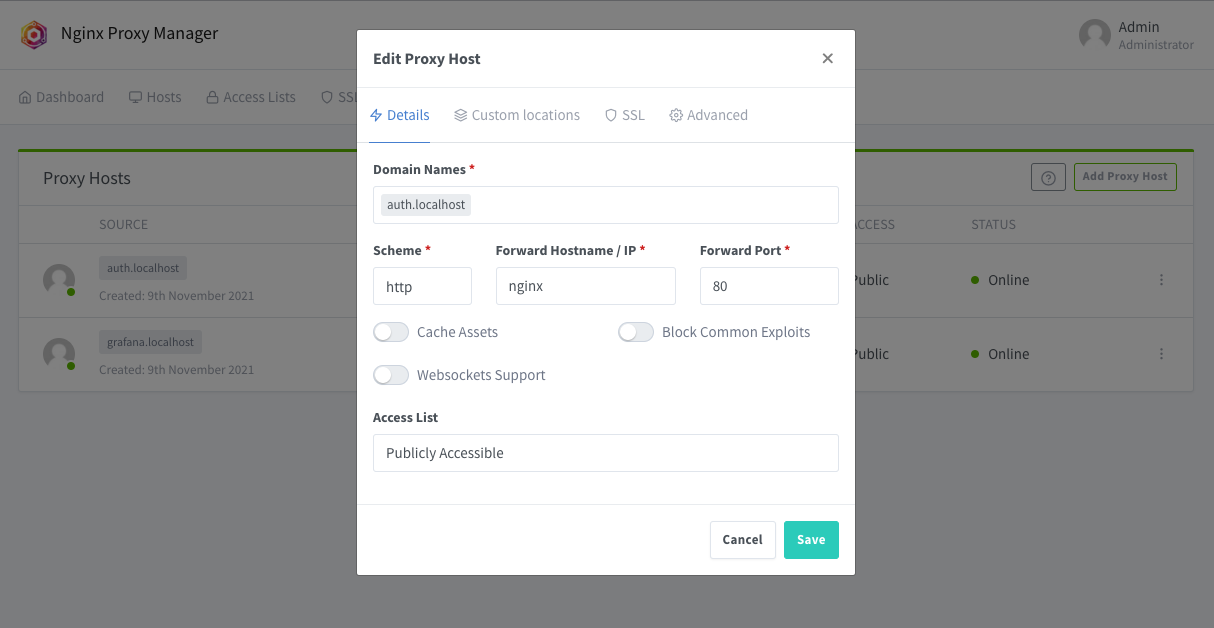
click “Add Proxy Host”, with the following settings for grafana. The example uses
grafana.localhostfor the domain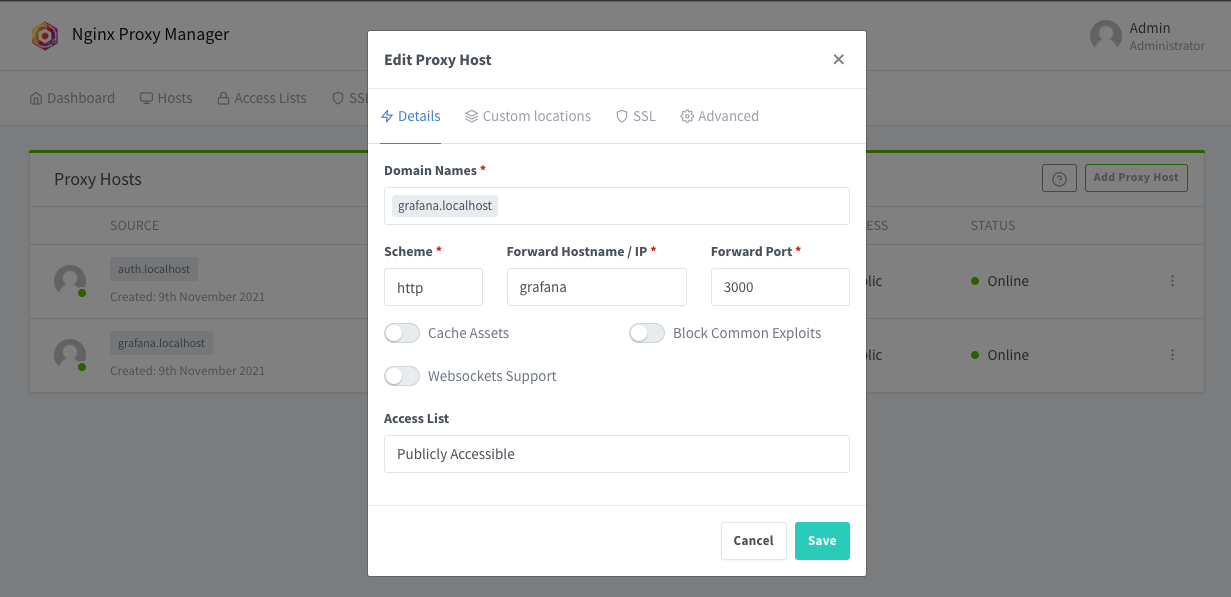
Congrats! You should now see auth running at http://auth.yourdomain and grafana at http://grafana.yourdomain!
SSL Guide
Unless you’re running auth locally in docker for testing, you should be using SSL. Thankfully, setting up SSL in nginx Proxy Manager takes about three clicks.
Edit your existing proxy host, and go to the SSL tab. Select “Request a new SSL Certificate” from the drop down.
Now, enable “Force SSL” and “HTTP/2 Support”. (NOTE: Do not enable HSTS unless you know what you’re doing. This will force your domains to only work with SSL enabled, and is cached extremely hard in browsers. )
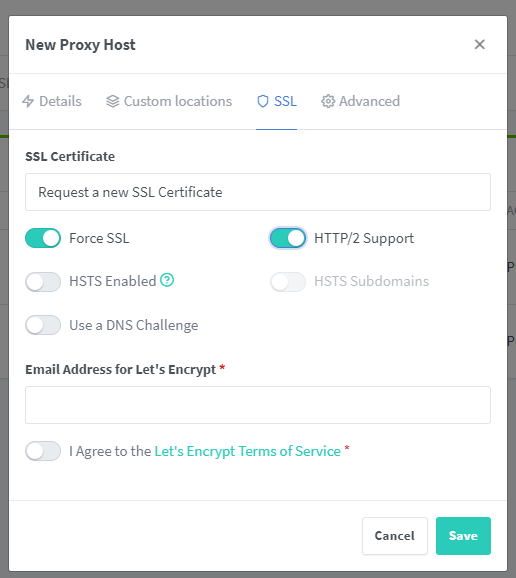
(optional) select “Use a DNS Challenge”. This is not a required option, but it is recommended if you use a supported DNS provider. You’ll then be asked for an API key for the provider you choose. If you use Cloudflare, you’ll probably have issues getting SSL certs unless you use a DNS Challenge.
The email address here will be used to notify you if there are issues renewing your certificates.
Repeat for any other services, like grafana.
That’s it! You should now be able to access your auth install at https://auth.yourdomain
Adding extra packages
There are a handful of ways to add packages:
Running
pip installin the containersModifying the container’s initial command to install packages
Building a custom Docker image (recommended, and less scary than it sounds!)
Using a custom docker image
Using a custom docker image is the preferred approach, as it gives you the stability of packages only changing when you tell them to, along with packages not having to be downloaded every time your container restarts
Add each additional package that you want to install to a single line in
conf/requirements.txt. It is recommended, but not required, that you include a version number as well. This will keep your packages from magically updating. You can lookup packages on https://pypi.org, and copy from the title at the top of the page to use the most recent version. It should look something likeallianceauth-signal-pings==0.0.7. Every entry in this file should be on a separate lineModify
docker-compose.yml, as follows.Comment out the
imageline underallianceauthUncomment the
buildsectione.g.
x-allianceauth-base: &allianceauth-base # image: ${AA_DOCKER_TAG?err} build: context: . dockerfile: custom.dockerfile args: AA_DOCKER_TAG: ${AA_DOCKER_TAG?err} restart: always ...
run
docker compose --env-file=.env up -d, your custom container will be built, and auth will have your new packages. Make sure to follow the package’s instructions on config values that go inlocal.pyrun
docker compose exec allianceauth_gunicorn bashto open up a terminal inside your auth containerrun
allianceauth update myauthrun
auth migraterun
auth collectstatic
NOTE: It is recommended that you put any secret values (API keys, database credentials, etc) in an environment variable instead of hardcoding them into local.py. This gives you the ability to track your config in git without committing passwords. To do this, just add it to your .env file, and then reference in local.py with os.environ.get("SECRET_NAME")
Updating Auth
Base Image
Whether you’re using a custom image or not, the version of auth is dictated by $AA_DOCKER_TAG in your .env file.
To update to a new version of auth, update the version number at the end (or replace the whole value with the tag in the release notes).
run
docker compose pullrun
docker compose --env-file=.env up -drun
docker compose exec allianceauth_gunicorn bashto open up a terminal inside your auth containerrun
allianceauth update myauthrun
auth migraterun
auth collectstatic
NOTE: If you specify a version of allianceauth in your requirements.txt in a custom image it will override the version from the base image. Not recommended unless you know what you’re doing
Custom Packages
Update the versions in your
requirements.txtfileRun
docker compose buildRun
docker compose --env-file=.env up -d